Microsoft Entra cloud-first IAM: Options for transitioning from on-premises MIM to Microsoft Entra focused solutions
Many of Oxford Computer Group’s customers around the world are talking to us about the best way to move towards a cloud-first Identity and Access Management (IAM) implementation – migrating the heart of identity management in the organization from on-premises systems like Microsoft Identity Manager (MIM) to the cloud (Microsoft Entra ID).
Want to know more? James held a webinar to expand further.
WATCH THE RECORDING
The motivations for this are various, including:
- A general “cloud-first” strategy
- A recognition that the “hairpin” of importing cloud-hosted HR data to an on-premises system, only to send the data to the cloud again, often makes little sense
- The need to integrate better with a cloud-focused monitoring and reporting approach, including the use of Copilot AI assistants
- Dissatisfaction with the existing IAM solution, caused by, perhaps, a lack of investment over time, meaning that the IAM system has not evolved with the systems it manages and their business needs. In addition, there may be a lack of staff, skills, or documentation to fix and manage it (these are, of course, not (yet) Oxford Computer Group customers!)
While the need for “more cloud” is widely (but not universally!) accepted, the “legacy” systems in our private networks, whether on-premises or hosted in cloud IaaS (Infrastructure as a Service), are not going away soon – and while we plan and build for the future, we must make sure that we do not neglect the security and efficiency of these systems. This is why I, and my architect colleagues at Oxford Computer Group, are engaged continuously in discussions with almost every customer concerning “cloud-first identity management” and even, in some cases, a “cloud-only” strategy. For most customers, though, a hybrid identity environment will remain for the foreseeable future.
Microsoft Entra ID has come a long way since I wrote this article just over a year ago, advocating a cloud-centric approach – and we have seen the release of some major new functionality in Microsoft Entra ID in the last 6 months. There will be a continuous stream of features arriving in the future (which cannot be said for MIM), and for many (if not most) MIM users, a wholesale move to Microsoft Entra ID is a realistic option – including those with a hybrid environment.
So how do we do this? What is the best way for organizations that currently use MIM to plan to transition their identity and access management to cloud-first?
I have put together this article as a kind of roadmap for MIM users – I identify a set of scenarios and describe a transitional approach for each of them.
At Oxford Computer Group, we believe there are 5 main scenarios, each with its own set of considerations. However, each organization is different, with its own intricate challenges, and we would recommend you have a chat with us (as IAM experts with decades of experience) before deciding on a final transition route.
Before we begin, a word about licensing. The impact of a functional requirement on the required licences is clear – but the starting position is not, and nor is the future construction of licensing. So, while we can be clear on “at present, you need Microsoft Entra ID P1 licences for this scenario, and Microsoft Entra ID P2 for that”, we can’t know what you already have, and hence we can’t (and therefore won’t) make any comment on the licensing costs of a given solution. We will simply say what licences are generally required (at the time of writing).
Want to know more? James held a webinar to expand further.
WATCH THE RECORDING
Scenario 1 – Complete migration to Microsoft Entra ID
Microsoft Entra ID has evolved enough that we can confidently say that many organizations are already in a position to migrate their complete identity management solution from MIM to the cloud, and subsequently retire MIM.
This is likely to be relevant if you:
- Use the MIM synchronization engine to read data from a single HR system, with a possible additional source for external contractors, using this information to provision users and groups (perhaps with automatic memberships) into Active Directory (AD)
- Use little or no functionality from the MIM Service/Portal
- Do not have sophisticated process or logic requirements to address downstream on-premises systems
Current implementation
The following diagram shows an example of a current implementation matching this scenario:
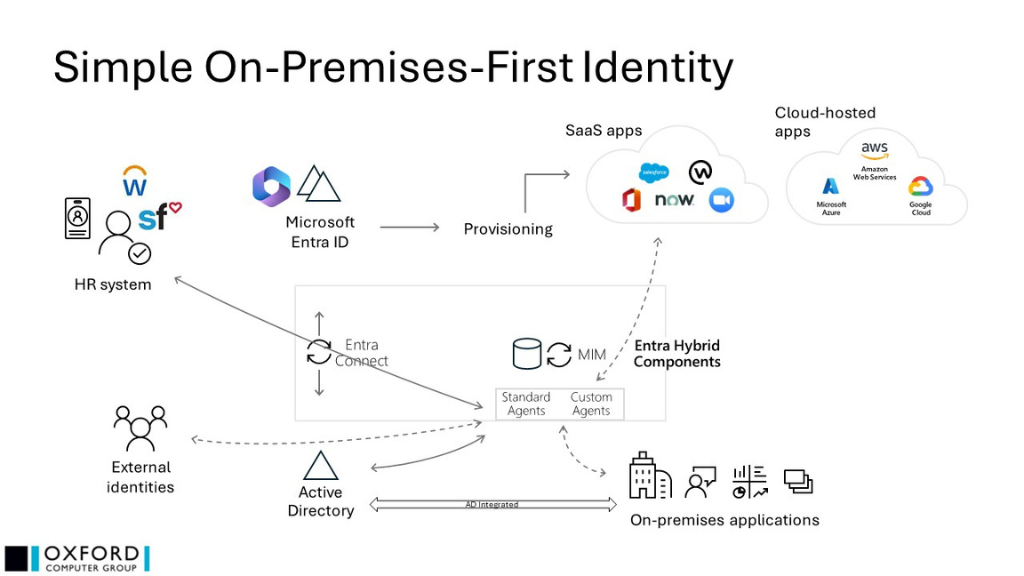
- MIM is responsible for reading HR data and populating AD
- Other applications are generally integrated with AD for authentication and authorization
- The dotted arrows represent possible additional functionality in use – the more complex this is, the more difficult complete migration will be
- Microsoft Entra Connect is responsible for populating Microsoft Entra ID (to support Microsoft 365, for example), using AD as the source
- Either, or both, of Microsoft Entra ID and MIM may also be managing cloud SaaS applications
- “Entra Hybrid Components” refers to the various server-based components included in Microsoft Entra Premium licenses which support hybrid scenarios, including MIM, Microsoft Entra Connect, and the Entra Provisioning (“ECMA2”) host
Future implementation
In this scenario, a wholesale migration of MIM functionality to Microsoft Entra ID with P1 licences is generally realistic – allowing MIM to be retired – and a solution might look like this:
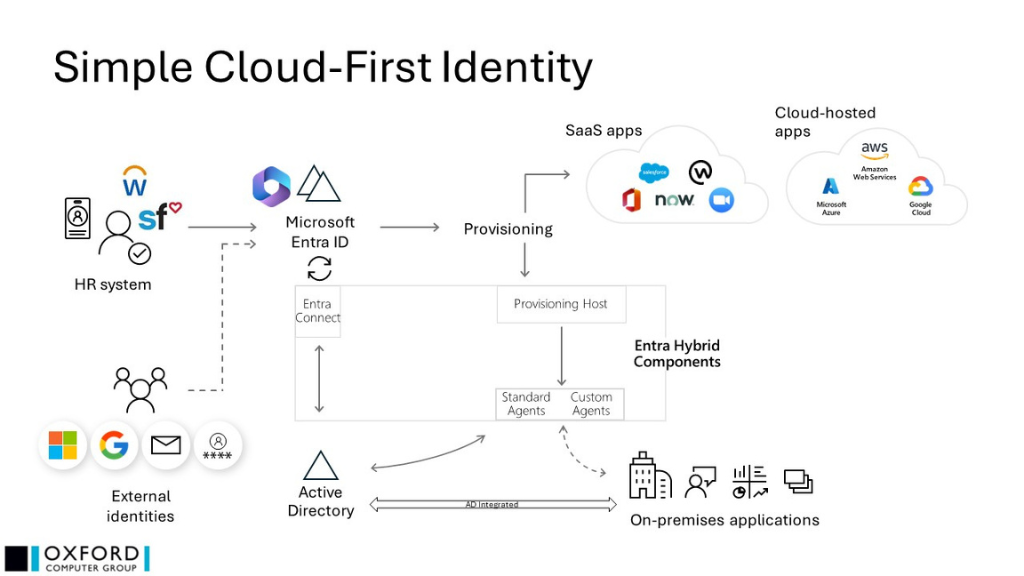
- MIM has been replaced by Microsoft Entra ID’s capabilities: inbound HR and outbound provisioning and management both to SaaS applications (directly) and on-premises applications (via a lightweight provisioning host and its various agents)
- Federated integration of externally hosted digital identities is a native feature of this architecture, opening a variety of new possibilities
- Microsoft Entra P1 licences will be required at a minimum
- Microsoft Entra Connect may or may not be required
- Bear in mind that to support cloud-only scenarios, you will need cloud-managed devices (for example, Microsoft Intune)
Your next steps
If this sounds like your implementation, Oxford Computer Group can provide a quick, and often fixed-price, migration approach. Please contact us to organize an initial Design Workshop so we can understand your current implementation. Following this, we will determine whether a standardized, fixed-price approach or a more customized approach is right for you, and we can then move on to assist you in migrating your current MIM/IAM functionality quickly to Microsoft Entra ID.
Scenario 2 – Cloud-first hybrid
This scenario accommodates more IAM complexity than the previous one. While it is possible (and common) to implement sophisticated processes and logic in Microsoft Entra ID, the economic imperative may be to keep using the existing MIM solution, rather than (expensively) re-engineering the solution into Microsoft Entra ID (“if it ain’t broke, don’t fix it”).
This is also relevant to customers who want to pursue an evolutionary approach – move appropriate functionality to Microsoft Entra ID, keep the existing technical logic in MIM, and repeat this process as each of the on-premises apps reaches its end-of-life, or is migrated itself into a SaaS version.
This will be of interest to you if:
- The current MIM solution uses complex logic for precedence and/or transformations (of attributes and/or schema)
- MIM is being used in addition to Microsoft Entra Connect to manage Microsoft Entra ID (e.g. guest accounts, Teams)
- MIM is managing other SaaS applications
- The combination of business logic in both Microsoft Entra ID and MIM is proving to be difficult to manage
- You are looking for an identity governance solution (attestation, separation of duties)
- You initially want to continue to create AD users first, with Microsoft Entra ID users remaining optional while maintaining the option to go to cloud-first at a later date
Current implementation
This scenario might initially look like this:
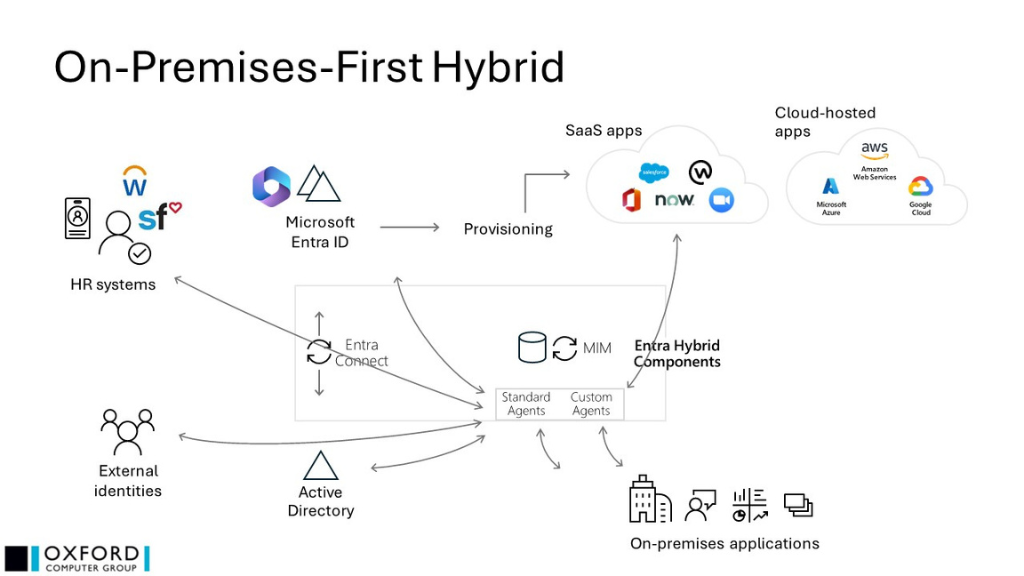
- MIM is importing HR data, often from multiple sources, sometimes with complex logic concerning precedence, orchestration, and issues such as secondment, and various absence scenarios (both personal and regulatory)
- MIM is integrated with Service Desk application(s), commonly delivering identities and roles (which are then managed by the Service Desk) and retrieving management decisions (group memberships, role assignments) from the Service Desk for downstream implementation
- MIM is managing some on-premises applications using custom agents, often with rich logic in both attribute flows and data handling in the agent itself
- MIM is importing data concerning external identities (e.g. contractors, customers) and applying appropriate logic
- Microsoft Entra Connect is responsible for creating users and group memberships in Microsoft Entra ID to implement decisions made on-premises
- There may be some direct management of SaaS applications from Microsoft Entra ID
Future implementation
A possible implementation might look like this:
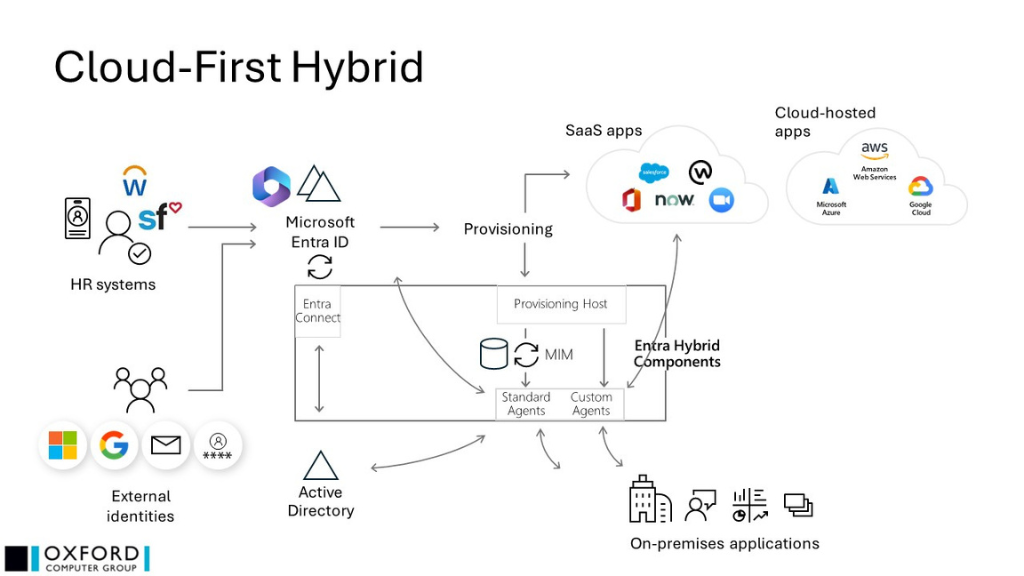
- MIM is receiving (as necessary) provisioning instructions and attribute changes from Microsoft Entra ID – replacing the upstream HR agents that were previously in MIM (hence “cloud-first”). Where possible, however, the provisioning instructions are simply carried out by the provisioning host’s own agents
- In complex scenarios the HR → Microsoft Entra ID flows may need to be customized, providing pre-import consolidation
- This architecture allows the progressive migration of MIM to Microsoft Entra ID, without the cost, risk, and pressure of a big-bang project
- In many cases, the business logic will be consolidated in Microsoft Entra ID – decisions on provisioning, licensing, approvals, and governance are made by Microsoft Entra ID. Downstream technical implementation, the carrying-out of decisions made in Microsoft Entra ID, may be performed either by Microsoft Entra ID itself or by existing MIM components, whichever is appropriate
- The solution benefits from Microsoft Entra ID’s capabilities concerning external identities, including B2B and B2C scenarios
- You are likely to require Microsoft Entra ID P2 licences and, depending on your requirements, licensing for lifecycle workflows with additional Microsoft Entra ID Governance licences
Oxford Computer Group is currently working with many customers in this situation. We understand Microsoft Entra ID and MIM in depth so we know what we can move to Microsoft Entra ID and what needs to continue to be done in MIM, at least for the time being, while plans to enable further migrations are made.
Want to know more? James held a webinar to expand further.
WATCH THE RECORDING
Your next steps
If this sounds like your implementation, contact Oxford Computer Group to organise a Design Workshop to understand your current implementation including giving your current MIM implementation a health check. We can then recommend an approach to migrate appropriate functional components to Microsoft Entra ID, along with plans to help maintain your MIM implementation so it continues to run smoothly and/or train your staff in MIM.
Scenario 3 – Identity-as-a-Service (IDaaS) hybrid
Some of our customers have a sophisticated identity implementation, as discussed in Scenario 2 above, but also want to remove their reliance on MIM completely. Additionally, such implementations may include custom user interfaces (providing, for example, attestation and other governance functionality). This scenario addresses these needs:
- You want a “single pane of glass” into your IAM world, for example with custom user and administrative portals for the whole solution
- You have many workflows to design and manage, including, for example, workflows with sophisticated approval and delegation requirements
- MIM cannot provide the required functionality
- Maintaining MIM in addition to a cloud solution is not feasible (for financial, operational, or political reasons)
- Microsoft Entra ID remains the strategic core of the organization’s identity management landscape, but additional functionality is required
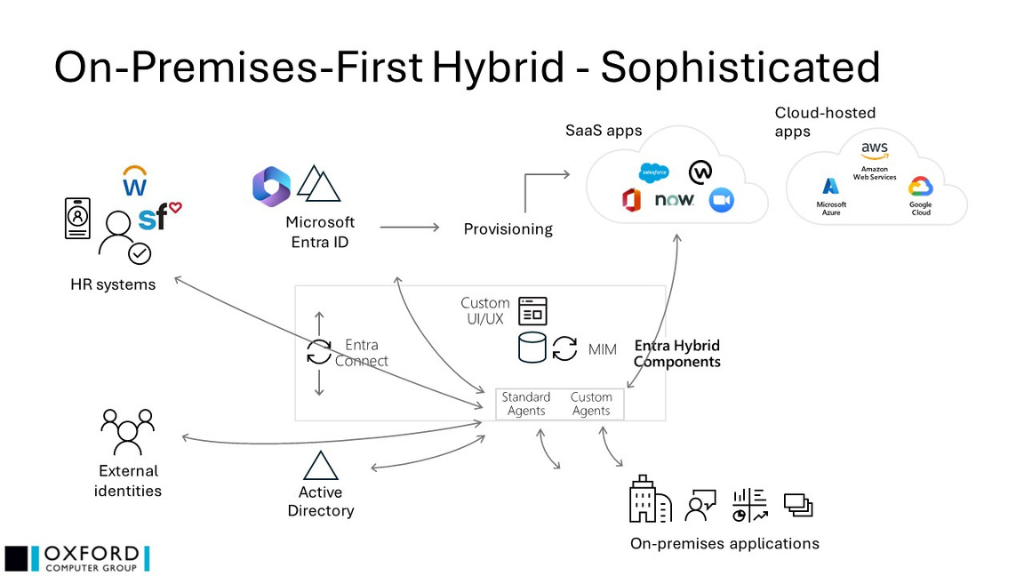
Future implementation
Oxford Computer Group incorporates a number of different 3rd party IDaaS platforms into customer solutions, all of which maximize the use of Entra ID’s native capabilities, while enhancing them with additional functionality, such as custom UI/UX, hierarchical role and permission inheritance, workflow preview and rollback, management of fine-grained access, and detailed reporting of roles and permissions, and usage against reference frameworks.
This solution may be broadly shown thus:
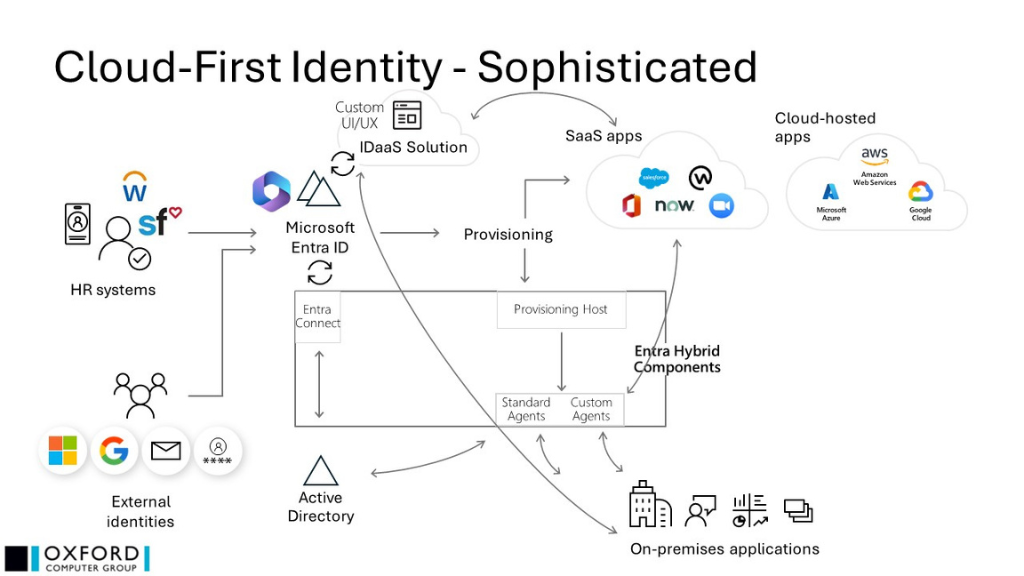
- The IDaaS solution is tightly integrated with Microsoft Entra ID, delivering (for example) the output (in the form of group memberships or access package assignments) of role-based calculations which result from (potentially multiple) organizational assignments and complex segregation of duties (SoD) requirements
- Microsoft Entra ID is providing as much provisioning capability as appropriate, while IDaaS is supporting this with native functionality where necessary
Your next steps
For more information, contact Oxford Computer Group to discuss how an IDaaS 3rd party solution that maintains Microsoft Entra ID at its core will work best for your implementation and requirements. We work with several trusted partners, and your local Oxford Computer Group company will help you make the right choice.
Scenario 4 – Private cloud only
Several of our customers (many of them government/defence entities) are simply not allowed to use cloud services at all, or at least not for security-sensitive activities such as authentication and authorization. They do, however, need a roadmap to a future beyond MIM.
Current implementation
These implementations vary widely in their complexity, from single instances of MIM performing all functions, to multiple MIM instances with each instance responsible for a network partition in a deeply layered security structure. The shared requirement, however, is to maintain this functionality securely without a long-term dependency on the MIM product.
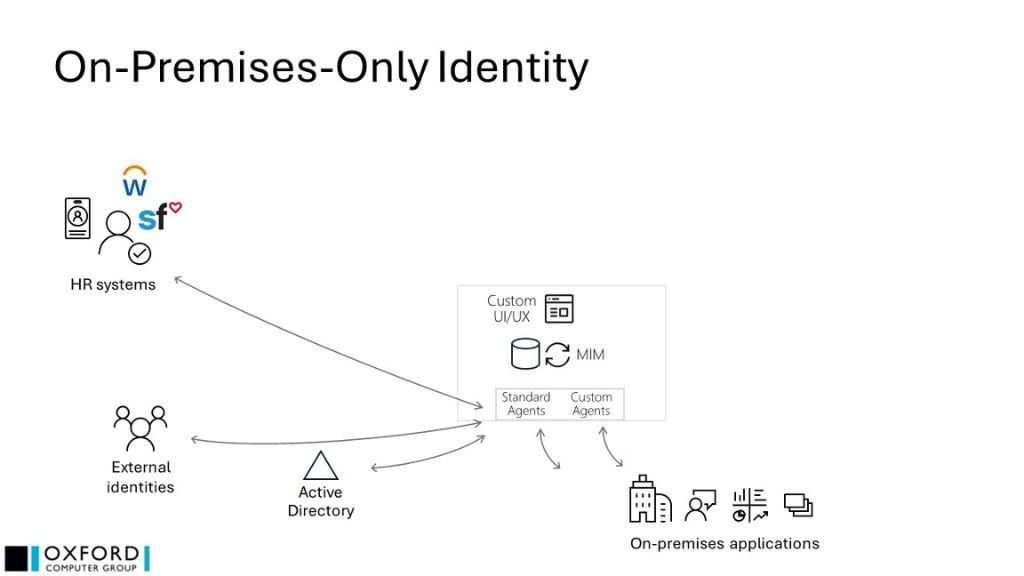
Future implementation
In the absence of a public cloud implementation, the replacement for MIM in this case is 1:1, so the solution illustration is very similar.
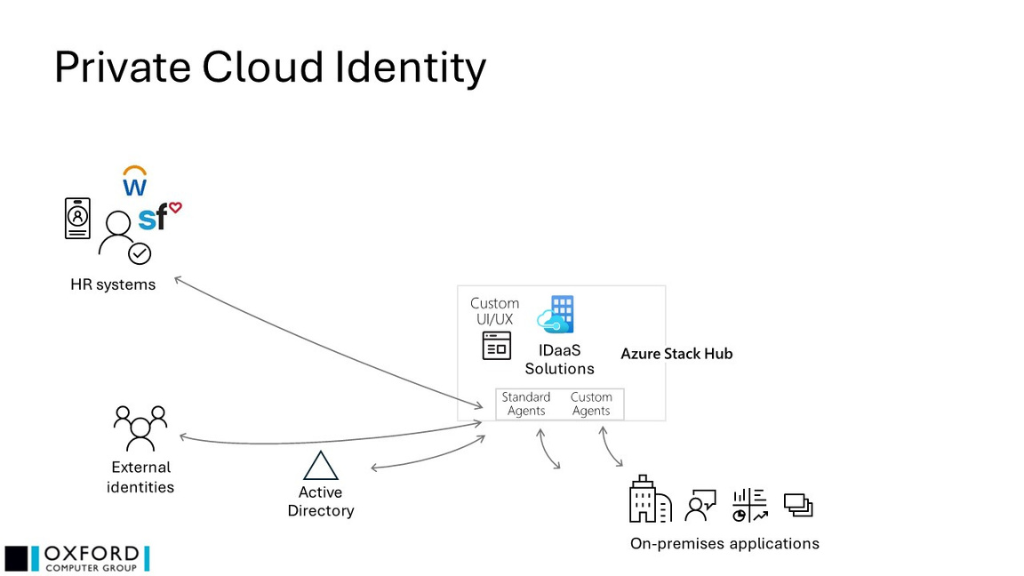
- The solution may be as simple as replacing a single MIM instance with a single instance of a replacement product, or it may need to integrate with a more elaborate private cloud concept, based, for example, on Microsoft’s Azure Stack Hub
- In either case, the replacement product will ideally be able to import the existing MIM configuration to make the migration as easy as possible
- It is possible that the existing MIM solution simply remains in place until circumstances change, in which case it will need to be maintained and supported
Your next steps
In this case, we suggest you contact Oxford Computer Group to find out how we can help you support your MIM implementation in the future and/or give your staff the training they need to keep MIM working well for you. For migration guidance, your local Oxford Computer Group company can help you make the appropriate choices and approach.
Scenario 5 – Maintain status quo, plan for the future
There will be some organizations who have read this far and do not feel that any of the above scenarios are relevant. For example, they may have:
- Complex schema requirements that exceed the extensibility of Microsoft Entra ID
- Extremely complex consolidation and/or precedence requirements in the upstream data flows (i.e., from multiple HR systems)
- Complex integrations between MIM and the Service Desk which would be costly and complex to try to replace at this stage
Your next steps
Contact Oxford Computer Group to arrange a workshop so we can fully understand your implementation and identify any parts of your system that you can move to the cloud, or otherwise enhance. However, while it is likely that you will need to stick with your MIM implementation for now, stay in touch with us, so we can plan the best possible implementation of a future system, and let you know when Entra ID can handle this level of complexity.
In the meantime, Oxford Computer Group can help you support and manage your MIM implementation for the future and/or train your staff.
Contact Us
Summary
Identity management is an important part of any organization and it is crucial that it is set up correctly to ensure your organization stays secure. Moving to the cloud may be part of this process for some or all the functionality for your organization – but we would recommend you understand the whole picture before you start.
Want to know more? James held a webinar to expand further.
WATCH THE RECORDING
For customers operating in a hybrid environment, Oxford Computer Training’s in-person, private “Mastering security in Microsoft hybrid environments” workshop is an invaluable session to make sure that no security issues arise. This workshop, designed in conjunction with Vattenfall, a prominent European multinational utility company that takes its identity security very seriously, delves into the intricacies of vulnerabilities and remediations within the Microsoft hybrid environment, giving participants a comprehensive understanding of the evolving security landscape.
Oxford Computer Group is an international group of companies founded in 1983 with a long-standing reputation for excellence in identity and security solutions, support, and training. We are widely recognized as the leading provider of Microsoft identity solutions and have won Microsoft Partner of the Year awards eight times.
Note: We are happy for you to use the text and graphics of this article in your internal communications, but we would appreciate being credited and our logo remaining on the graphics.